Emerging Global Ransomware Attack Alert!
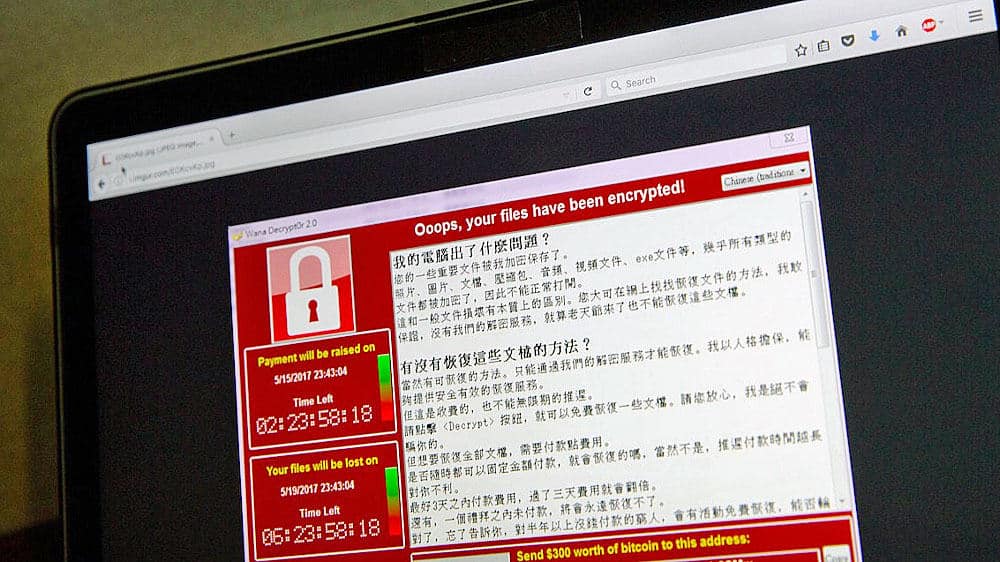
Ransomware attacks keep taking the unprepared world by surprise, and now the world has experienced one of the most severe ransomware outbreaks in history: WannaCrypt0r (also known as WannaCrypt, WannaCry, or WCry).
This ransomware has affected more than 200,000 computer systems including those at major companies such as FedEx, personal computers, ATM machines, and even hospitals, in over 90 countries.
This latest attack is so concerning that it has even captured the direct attention of the White House.
The good news is that right now, there has been a “Kill switch” initiated which drastically reduces the rate of the outbreak, but security experts are warning about other, more malicious versions on the horizon.
What is ransomware?
There are two types of ransomware: crypto-ransomware that encrypts files (rendering them unreadable), and screen-locking ransomware that locks the home screen.
In both cases, the authors of malicious software demand a ransom from its victims to access the files and device.
Ransomware is frequently spread via email: a cyber criminal sends an email with an attachment.
The unsuspecting user opens the document (or javascript file), which looks like gibberish.
Executing the document allows the ransomware to be secretly downloaded onto computers via a drive-by download. Once the payload is downloaded, the ransomware begins to encrypt all files, and replicate itself across unprotected networks.
What is so special about WannaCrypt0r?
In this case, it’s the ransomware’s way of spreading, which is more like a worm than a “normal” ransomware and its ability to self-propagate. That means that once it is on your system it will try and spread to another one on its own and by means of exploiting vulnerabilities that have either not been detected or patched yet. In the case of WannaCrypt0r, it’s a vulnerability called EternalBlue – one of the exploits recently released by Shadow Brokers in the leaked NSA tools archive.
Is my system protected?
The current version of WanaCrypt takes advantage of a flaw in the Microsoft Windows operating system which Microsoft has now patched. However, if your system is not actively being monitored, maintained and patched, MS17-010 could be missing leaving you vulnerable.
If you are currently enrolled in our Remote Care with patch management, or Enhanced Care plans, our team has already made every effort to verify that this patch has already been installed on your system and that you are protected.
Furthermore, we have already verified that all active firewalls and antivirus programs have the latest updates which will detect WanaCrypt and block its execution.
If you are not currently enrolled, call us today to find out how we can manage and protect your systems for you.
What do I do if I am infected?
In the worst case scenario, where you become infected, the first step is to unplug your system from the network and the internet.
Your next step is to check on your backups and come up with a plan to restore your data to a clean system.
You may have noticed that paying the ransom is not a recommended option as most victims are currently reporting making ransom payments without being able to regain access to their files.
Keep in mind these ransom payments are paid via Bitcoin, an untraceable, one-way form of internet currency.
This translates into a payment being sent to an unknown recipient and being at their mercy to take action.
How do I protect myself and my systems?
As ransomware becomes a household name, one thing is for certain: Global cybersecurity has reached a moment of emergency.
You need to make sure that you are aware of the latest updates, threats and tools, and that at the least bit, you are making sure that:
- You have a backup and disaster recovery system in place, which is tested and verified on a regular basis.
- All of your software up-to-date including the latest vendor patches (released multiple times a month).
- You have the proper antivirus and web protection, and its kept updated with the latest definitions (multiple times a day).
- Yu have the proper hardware based firewall installed, and that you are keeping it updated with the latest definitions to protect your network.
- Monitor all of your systems 24x7x365 to catch and prevent outbreaks.
If you feel like any of these items are above and beyond your capabilities or job description, contact us immediately!
Our team can help you manage every aspect of your IT and take your IT to the next level, so you can take your business to the next level.





