In the digital age, data is the lifeblood of businesses. It fuels operations, decision-making, and customer interactions. But there is a dark underbelly of this data-centric landscape. It’s the persistent threat of data breaches.
The repercussions of a data breach extend far beyond the immediate aftermath. They often haunt businesses for years. Only 51% of data breach costs occur within the first year of an incident. The other 49% happen in year two and beyond.
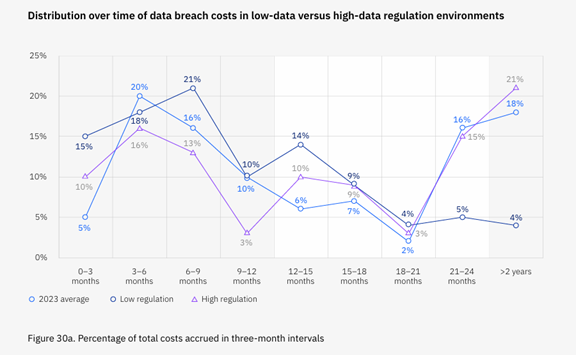
We’ll take a look at the long-term consequences of a data breach. As well as examine a real-world example. You’ll see how a single breach can have enduring implications. Ones that impact a business’s reputation, finances, and regulatory standing.
The Unseen Costs of a Data Breach
Introduction to the First American Title Insurance Co. Case
The 2019 cybersecurity breach at First American serves as a stark illustration. It reminds us of the far-reaching consequences of a data breach. In this case, the New York Department of Financial Services (NYDFS) imposed a $1 million fine. Cybersecurity sites announced the fine in the fall of 2023. The company’s fine was for failing to safeguard sensitive consumer information.
The breach exposed over 880 million documents. These files contained personal and financial data. The breach represented a significant violation of data protection standards.
This is one example of how costs can come long after an initial breach. Here are some other ways security incidents can haunt businesses for years.
Lingering Impacts of a Data Breach
Financial Repercussions
The financial toll of a data breach is significant. Immediate costs include things like:
- Breach detection
- Containment
- Customer notification
Beyond those, businesses face long-term expenses. These relate to legal battles, regulatory fines, and reparations. Regulatory penalties are just one facet of the financial repercussions. Others include potential legal actions from affected individuals. As well as class-action lawsuits adding to the monetary strain.
Reputation Damage
The impact on a business’s reputation is arguably the most enduring consequence. Customers lose trust in a company’s ability to protect their sensitive information. This loss of trust can result in a decline in customer retention. As well as acquisition difficulties and long-lasting damage to the brand image.
Rebuilding a tarnished reputation takes time. It also takes concerted efforts. These may involve public relations campaigns and enhanced security measures. These actions help assure stakeholders of renewed commitment to data protection.
Regulatory Scrutiny
Regulatory bodies increasingly hold businesses accountable for safeguarding consumer data. A data breach triggers regulatory scrutiny. This may lead to fines and ongoing compliance requirements.
Regulatory authorities take a stringent stance on data security. As well as on companies that fail to meet cybersecurity standards. The fallout includes financial penalties. As well as increased oversight and mandatory security improvements.
Operational Disruption
The aftermath of a data breach disrupts normal business operations. Companies must take remediation efforts and put in place enhanced security measures. These can divert resources away from core business functions.
The company feels the impact across departments, affecting productivity and efficiency. The ripple effect of operational disruption can extend for years. This impedes growth and hinders the organization’s ability to adapt to market changes.
Customer Churn and Acquisition Challenges
A data breach often leads to customer churn. Individuals lose confidence in the business’s ability to protect their data. Acquiring new customers becomes challenging. Potential clients are wary of associating with a brand that has suffered a breach. The prolonged effects on customer acquisition can hinder the company’s growth. As well as its market competitiveness.
A Cautionary Tale for Businesses Everywhere
The repercussions of a data breach extend far beyond the immediate incident. They can impact the financial health and reputation of a business for years. As well as its regulatory standing.
The frequency and sophistication of cyber threats continue to rise. Proactive cybersecurity measures are not just a necessity. They are a strategic imperative for safeguarding the long-term success of businesses.
The true cost of a data breach is not always immediately evident. It’s a complex interplay of things like:
- Financial penalties
- Reputation damage
- Regulatory consequences
- Operational disruption
These impacts can persist for years. It’s important to learn from real-world examples. As well as focusing on robust cybersecurity measures. This helps businesses mitigate the risks associated with data breaches. As well as safeguarding their immediate interests and their long-term viability.
Need a Cybersecurity Assessment to Prevent an Unexpected Breach?
There are many ways that hackers can breach a network. From endpoints to cloud tools, you must run a tight security ship. Need some help?
Schedule a cybersecurity assessment today. This is the first positive step into understanding and addressing your risk. As well as avoiding the consequences of a data breach.
Give us a call today to schedule a chat.
This Article has been Republished with Permission from The Technology Press.





